International Location Safety & RiskPal Join Forces to Enhance Risk Management
We are delighted to announce a new partnership with International Location Safety (ILS), bringing an exciting new offering to travel risk management for Higher Education.
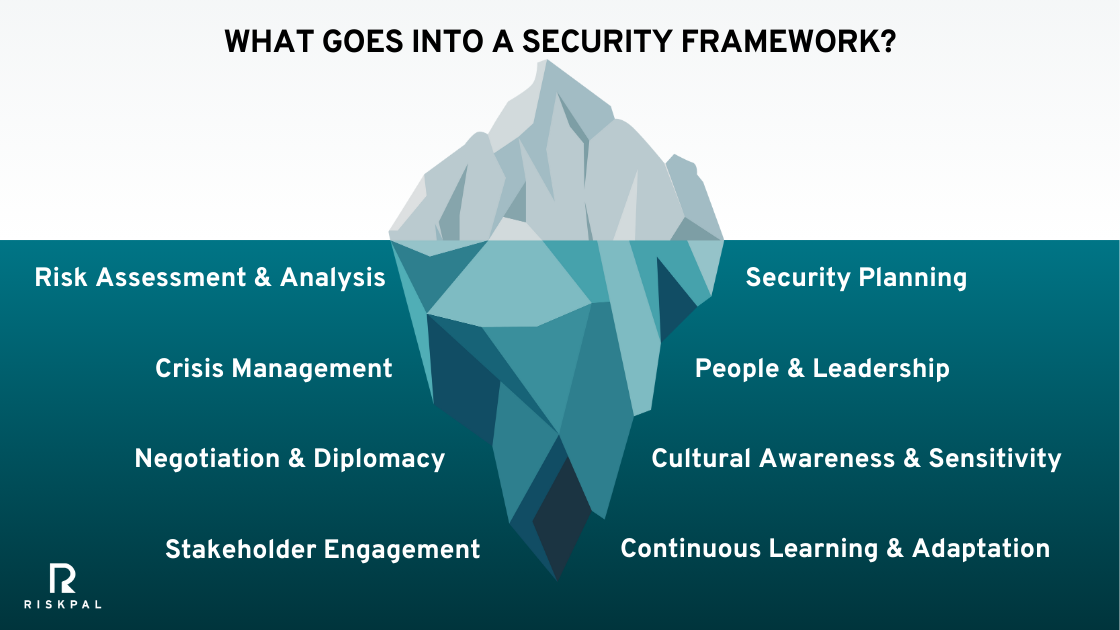
This partnership provides access to a complimentary combination of RiskPal’s cutting-edge risk assessment software and the ILS risk advisory and training services. With the new Help Desk service, clients can now have responsive, cost-effective travel risk management support from the ILS Risk Advisory team.
The partnership was born from a desire to improve the travel risk management services on offer to the Higher Education sector.
Here is what RiskPal’s COO, Tom Bacon, and ILS Managing Director, George Shaw, want you to know:


What This Partnership Offers Universities
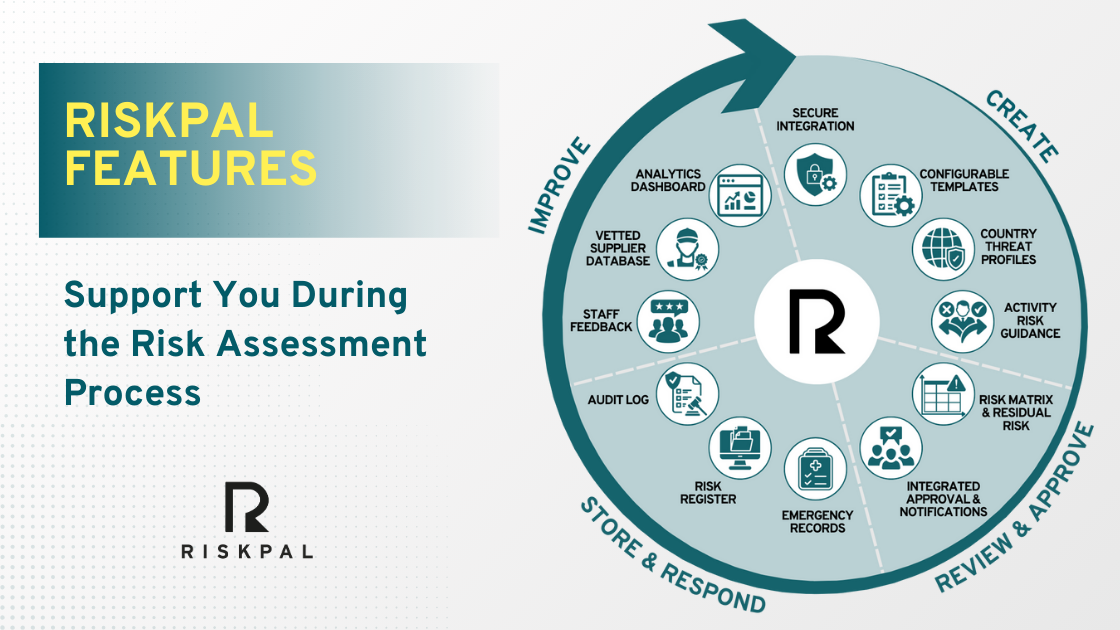
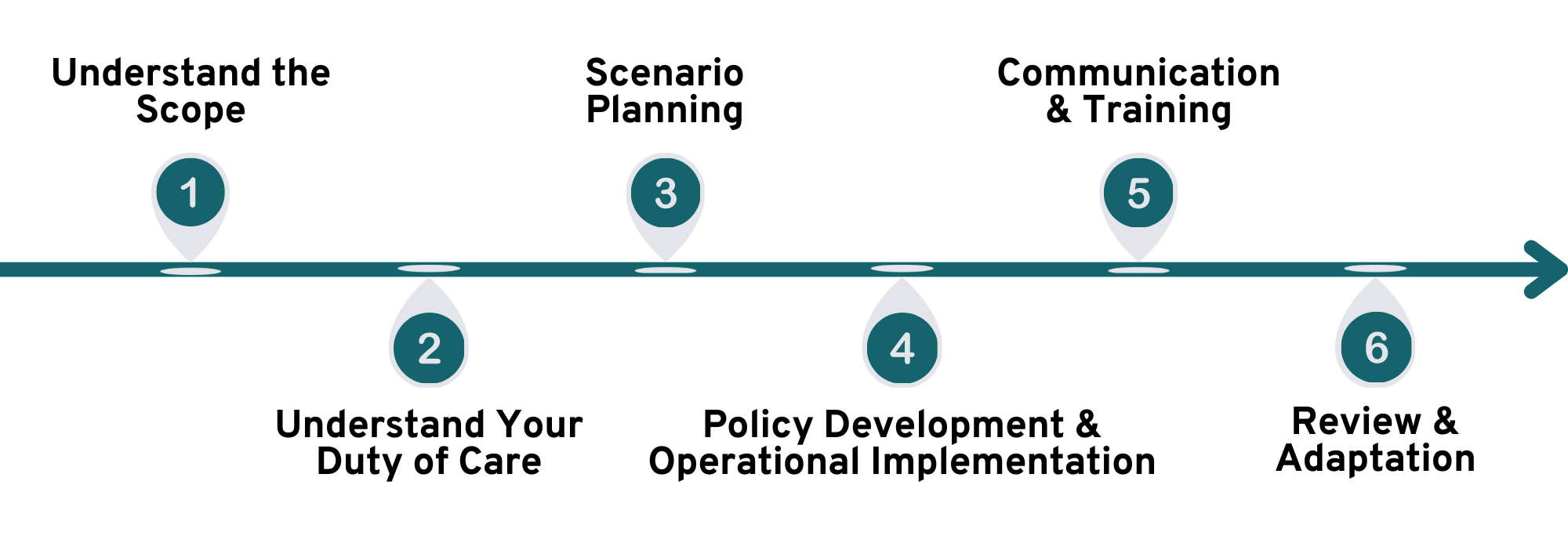
The ILS-RiskPal partnership gives universities access to an all-in-one pre-travel risk management solution, combining innovative technology with expert consultancy and training. Key benefits include:
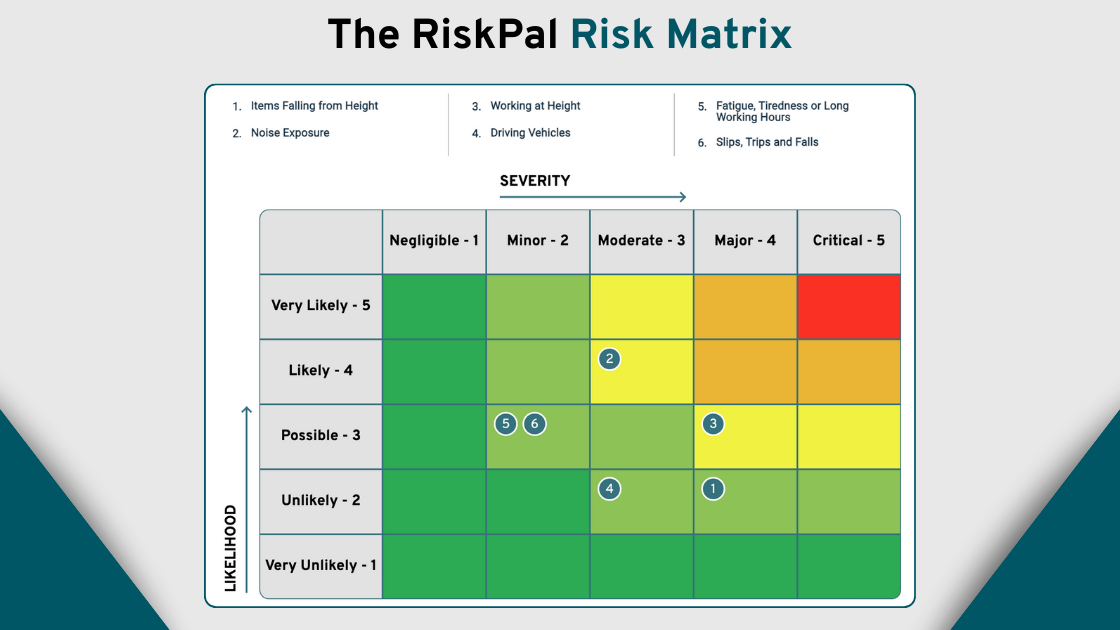
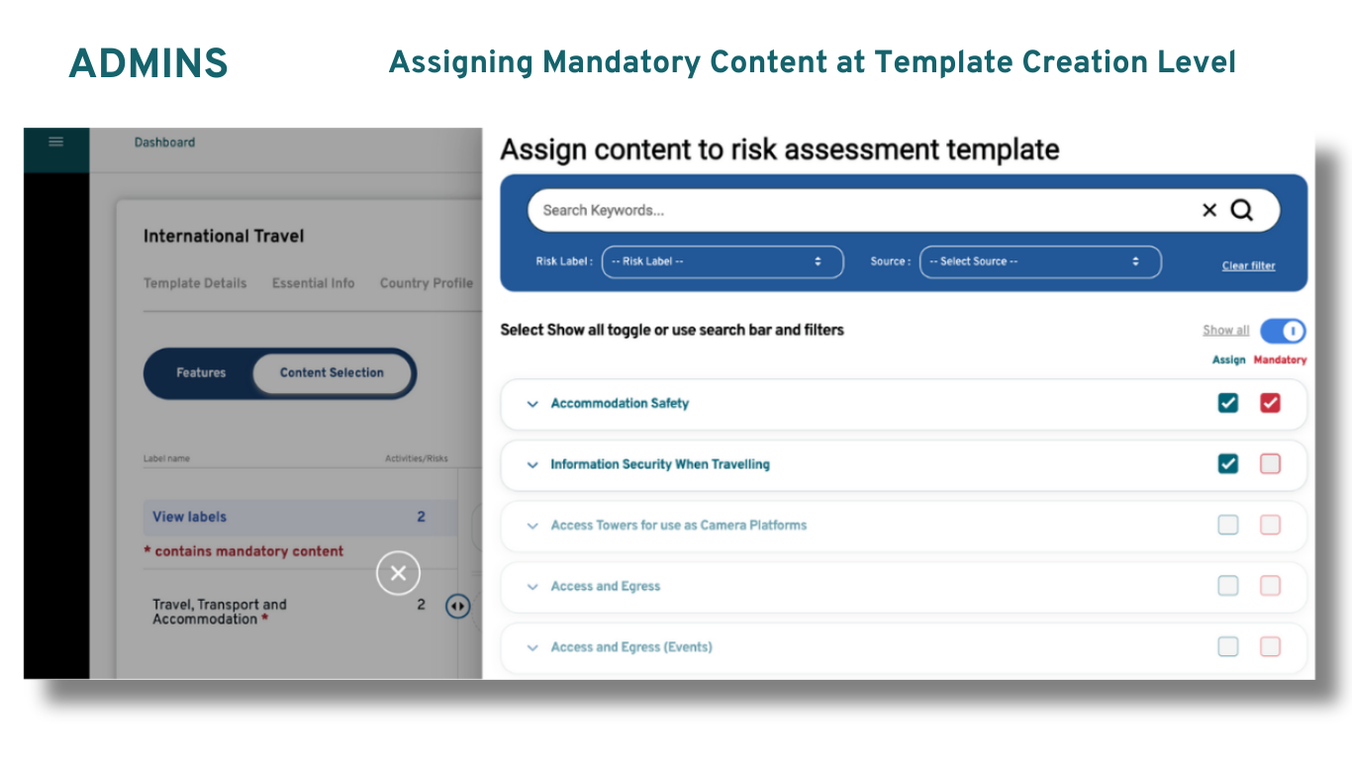
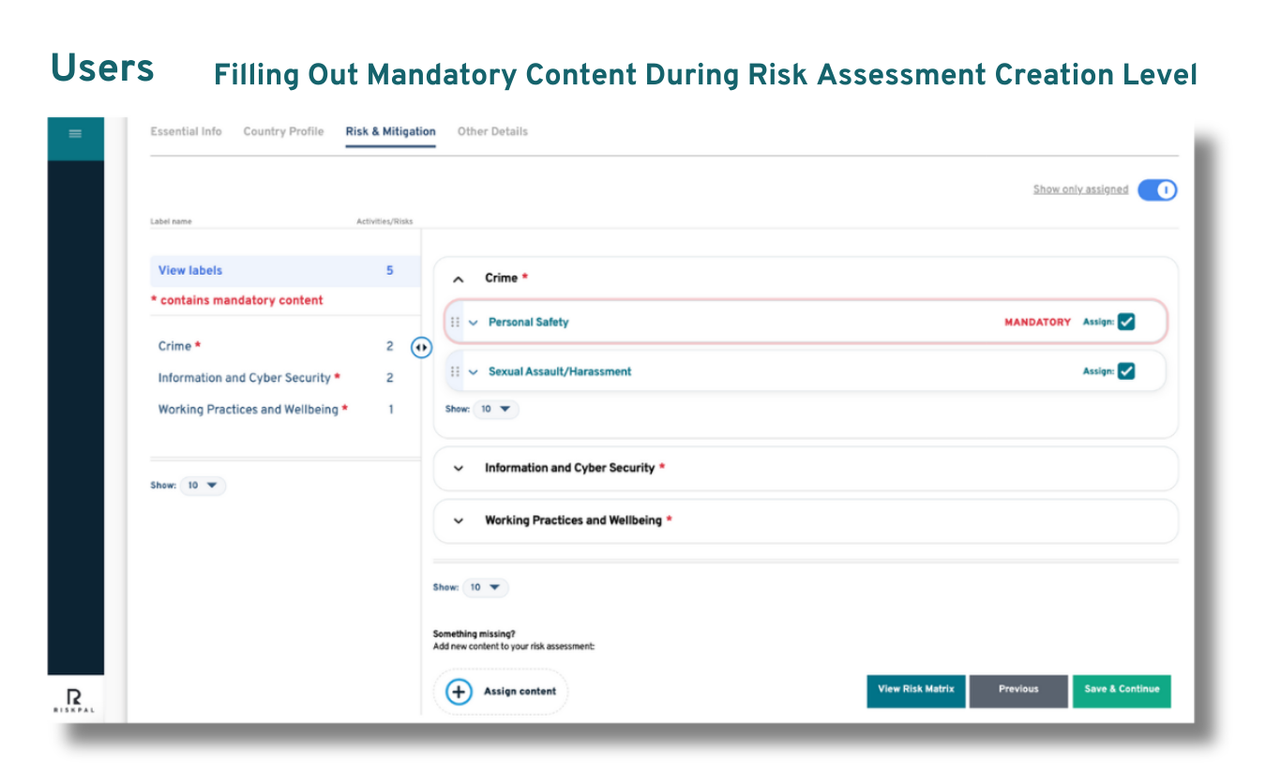
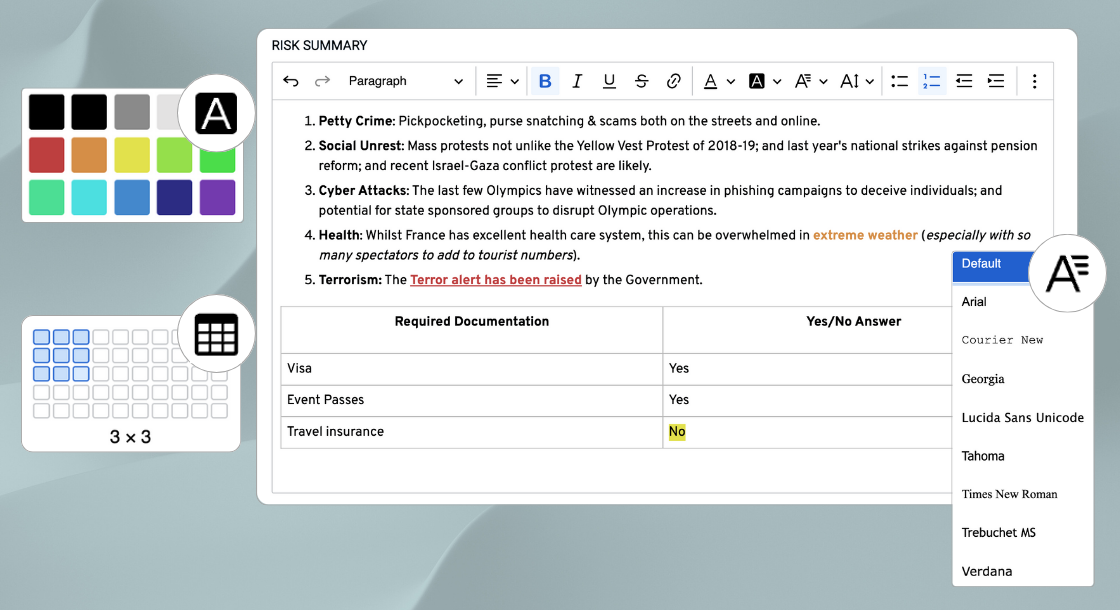
- Subscription to RiskPal’s leading risk assessment platform – featuring customisable templates, integrated approvals, and a comprehensive safety advice library.
- Retained access to the ILS Helpdesk – offering expert consultancy support and risk management advice for specific destinations and activities.
- ILS’ in-person and online travel safety training – equipping students and staff with essential skills to navigate risks effectively.
Elevate Your University Travel Risk Management
With RiskPal and ILS, university travel managers now have access to an unparalleled combination of cutting-edge risk assessment software and expert advisory support. Whether you need on-the-spot guidance for a complex trip or a scalable solution to enhance duty of care, our joint offering provides the tools and expertise to help you navigate travel risks with confidence.
Discover how our partnership can support you.